
Getty Images
When a London man found his Toyota RAV4’s front left bumper smashed and the headlight partially removed not once but twice in three months last year, he suspected the acts were senseless vandalism . When the vehicle went missing a few days after the second incident, and a neighbor found his missing Toyota Land Cruiser soon after, he discovered they were part of a sophisticated new technique to carry out keyless thefts.
It just so happened that the owner, Ian Tabor, is a cyber security researcher specializing in automobiles. While researching how his RAV4 was taken, he stumbled upon a new technique called CAN injection attacks.
The case of CAN malfunction
Tabor began by examining the “MyT” telematics system that Toyota uses to track vehicle anomalies known as DTCs (Diagnostic Trouble Codes). It turned out that his vehicle had recorded many DTCs around the time of the theft.
The error codes showed that communication between the RAV4’s CAN (short for Controller Area Network) and the electronic headlight control unit had been lost. These ECUs, as they are abbreviated, are found in virtually all modern vehicles and are used to control a myriad of functions, including wipers, brakes, individual lights, and the engine. In addition to controlling components, ECUs send status messages via the CAN to keep other ECUs informed of current conditions.
This diagram shows the CAN topology for the RAV4:
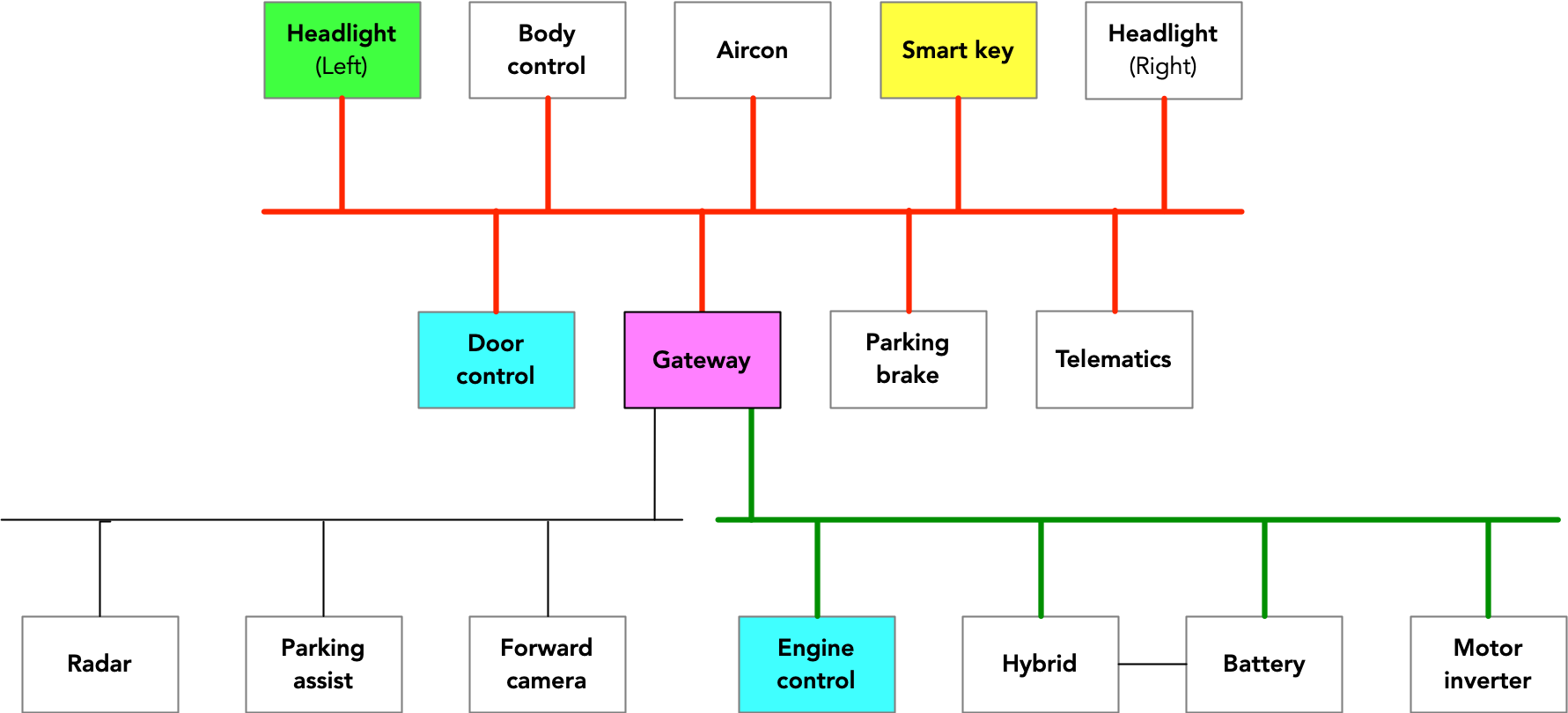
Diagram showing the CAN topology of the RAV4.
Ken Tindell
The DTCs showing the RAV4’s left headlight losing contact with the CAN weren’t particularly surprising, considering the thieves had ripped out the wires connecting it. More telling was the failure of many other ECUs at the same time, including those for the front cameras and hybrid engine control. Taken together, these errors did not indicate that the ECUs had failed, but that the CAN bus had malfunctioned. This left Taber looking for an explanation.
The investigator and the theft victim then turned to crime forums on the dark web and YouTube videos about how to steal cars. Finally, he found ads for so-called “emergency boot” devices. These devices were apparently designed to be used by homeowners or locksmiths to use when no key is available, but there was nothing stopping anyone else from using them, including thieves. Taber purchased a device advertised to jump-start several Lexus and Toyota vehicles, including the RAV4. He then proceeded to reverse engineer and, with the help of friend and fellow auto safety expert Ken Tindell, figure out how it worked in the RAV4’s CAN.
Inside this JBL speaker is a new form of attack
The investigation uncovered a form of keyless vehicle theft that no investigator had seen before. In the past, thieves have been successful using what is known as a relay attack. These hacks amplify the signal between the car and the keyless entry fob used to unlock and start it. Keyless fobs typically only communicate over distances of a few feet. By placing a simple portable radio device near the vehicle, thieves amplify the message that cars normally send. With enough amplification, the messages reach the nearby home or office where the key fob is located. When the fob responds with the cryptographic message that unlocks and starts the vehicle, the thief’s repeater transmits it to the car. With that, the thief walks away.
“Now that people know how a relay attack works…car owners keep their keys in a metal box (blocking the car’s radio message) and some car manufacturers now provide keys that ‘fall asleep if they are still for a few minutes (and so they won). “You don’t get the car radio message),” Tindell wrote in a recent post. “Faced with this defeat but unwilling to give up an activity lucrative, thieves turned to a new way to bypass security: bypassing the entire smart key system. They do this with a new attack: CAN Injection.”
Tindel links to this video, which it says captures a CAN injection heist in action.

2021 Toyota RAV4 – Stolen in less than two minutes.
The CAN injector that Tabor bought was disguised as a JBL Bluetooth speaker. This gives thieves cover in case the police or others become suspicious. Instead of carrying an obvious hacking device, the thief appears to be in possession of an innocuous speaker.

The CAN injector disguised as a JBL speaker.
Closer analysis revealed that there was much more. More specifically, there were CAN injector chips grafted onto the circuit board.

CAN injector chips encased in a resin globe grafted onto the JBL circuit board.
Ken Tindell
Tindell explained:
It turns out to be about $10 worth of components: a PIC18F chip that contains CAN hardware, plus pre-programmed software on the chip (known as firmware), a CAN transceiver (a standard CAN chip that converts digital signals from the PIC18F’s CAN hardware). to the analog voltages sent on the CAN wires) and an additional circuit connected to the CAN transceiver (more on that shortly). The device takes power from the speaker’s battery and connects to a CAN bus. A CAN bus is basically a pair of wires twisted together, and in a car there are several CAN buses joined together, either directly with connectors or digitally connected via a gateway computer that copies some CAN messages back and forth between the CAN buses. connected to
The theft device is designed to connect to the control CAN bus (the red bus in the wiring diagram) to impersonate the smart key ECU. There are several ways to reach the wires of this CAN bus, the only requirement is that the wires must reach the edge of the car for them to reach (wires buried deep in the car are impractical for thieves to reach that they try). steal a car parked on the street). The easiest route to access this RAV4 CAN bus is through the headlights: move the bumper away and access the CAN bus from the headlight connector. Another access would be possible – even drilling a hole in a panel where the twisted pair of CAN wires goes, cutting the two wires and splicing the CAN injector would also work, but the reduced value of a car with a hole. means thieves take the easiest route (Ian’s research found that most of these cars are destined for export, shipped via containers to locations in Africa).
When it first turns on, the CAN injector is doing nothing – it’s listening for a specific CAN message to let it know the car is ready. When it receives this CAN message it does two things: it starts sending a burst of CAN messages (about 20 times per second) and it activates this extra circuit connected to its CAN transceiver. The CAN message burst contains a “smart key is valid” signal and will be sent by the gateway to the engine management ECU on the other bus. This would normally cause confusion on the control CAN bus: CAN messages from the real smart key controller would collide with imposter CAN injector messages and this could prevent the gateway from forwarding the injected message. That’s where this extra circuit comes in: it changes the way a CAN bus works so that other ECUs on that bus can’t talk. The gateway can still listen for messages, and of course it can still send messages to the powertrain CAN bus. The burst repeats 20 times per second because the configuration is fragile, and sometimes the gateway doesn’t listen because its CAN hardware is rebooting (because it thinks that not being able to talk is an indication of a fault, which in in a way it is) .
There is a “Play” button on the housing of the JBL Bluetooth speaker and this is connected to the PIC18F chip. When this button is pressed, the burst of CAN messages changes slightly and tells the door ECU to unlock the doors (as if the “unlock” button on the wireless key had been pressed). Thieves can detach the CAN injector, get into the car and drive away.
Taber and Tindell have designed two defenses that they say would defeat CAN injection attacks. Tindell said they notified Toyota of the defenses, but have yet to hear back.


